Platform Offers Unified Coverage with Visibility, Monitoring, Posture, Compliance, and Threat Detection and Response Capabilities
- Rezonate uniquely protects both human and non-human identities through a unified, context-aware view of machine and human identities across the entire cloud and SaaS identity fabric.
- This visibility is combined with risk-driven actionability creating a continuum from human to non-human identities streamlining security efforts to prevent and defend against modern threats like supply chain attacks.
- The platform ensures end-to-end security coverage for programmable access credentials including API keys, OAuth tokens, service accounts, service principals, and cryptographic keys, and the humans who create them.
Rezonate, an innovator in identity-first security, today unveiled unified coverage from human to non-human identity security (NHI) with comprehensive capabilities: identity inventory and visibility, security posture, compliance, and identity threat detection and response (ITDR). The platform is leading the industry by taking a unified approach to managing both human and non-human identities and their interdependencies ensuring end-to-end visibility with risk-driven actionability across the identity fabric of an organization.
This press release features multimedia. View the full release here: https://www.businesswire.com/news/home/20240716267123/en/
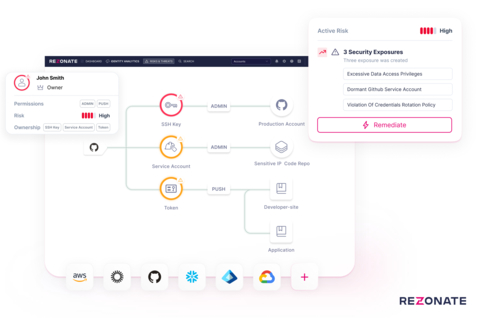
Rezonate leads the industry by taking a unified approach to managing both human and non-human identities and their interdependencies ensuring end-to-end visibility with risk-driven actionability across the identity fabric of an organization. (Graphic: Business Wire)
NHIs, also called machine identities, are digital access credentials that play a crucial role in securing company infrastructures while automating tasks and increasing business efficiencies. They are outnumbering human identities as much as 10 to 45 times according to Gartner, which creates a massive attack surface within organizations. If organizations do not monitor NHIs appropriately, they’re exposed to attacks that can rapidly spread throughout their systems without any humans realizing something’s changed.
Identity-First Approach to NHI Security
Rezonate is unique in offering a combination of visibility, monitoring, posture, threat detection and response, and compliance reporting for both non-human and human identities. Most other vendors only focus on NHI governance, administration, and lifecycle management. With discovery, inventory, and visibility into NHIs and associated users simultaneously on the same platform, Rezonate provides the most complete risk-driven, contextual insights enabling informed, proactive or even real-time decisions to be made. As a result, security, identity, and DevOps teams are better equipped to work together and prevent modern threats like supply chain attacks, or guided and automated remediation to accelerate time to security.
“During my experience in national cyber security operations and cybersecurity, I saw first-hand how defenders divide their world by adding different tools to solve the same problems. Attackers see this disparate complexity as a welcome challenge–in their world, the more chaos, the merrier,” said Roy Akerman, CEO and co-founder of Rezonate. “In modern threat tactics, attackers are targeting both machines and humans (the NHI creators and users) as part of the same attack. Securing NHIs and human identities separately increases friction, creates blindspots, and slows down the defenders. That's why we set out to address this rapidly growing challenge with a unified approach. Rezonate is the very first identity-centric security solution to offer end-to-end coverage of non-human identities and their creators with core capabilities for proactive posture and real-time threat detection and response.”
Protecting NHIs across IaaS, SaaS, and identity provider platforms, the platform delivers three core capabilities:
- Comprehensive Inventory and Visibility: Rezonate provides radically simple yet full visibility into NHIs across the entire attack path, including their authorization and authentication graphs, security controls, access conditions, and behavioral profiles. This detailed, real-time view includes critical information about each NHI, its permissions, entitlements, and the services it can access, facilitating better audit performance and accountability.
- NHI Hygiene and Security Posture Management: By understanding the risks and context associated with NHIs, Rezonate enables security, identity, and DevOps teams to make informed decisions. This includes ensuring NHIs have only the necessary permissions to prevent over-privileged access that attackers could exploit, facilitating proactive risk mitigation, and enhancing security posture.
- NHI Threat Detection & Response: Rezonate continuously monitors NHIs to detect abnormal behaviors and potential security breaches, including with owners of NHIs. Automated rules and alerts provide insights into NHI activities, enabling quick identification and mitigation of issues before they escalate into full-blown security breaches.
NHIs are the digital, automated, and programmable access credentials that play a crucial role in securing systems, managing access, and ensuring the integrity of digital environments while also helping automate tasks and increase business efficiencies. Typically coming in the form of API keys, OAuth tokens, service accounts, and secrets, they are the largest and fastest-growing part of a company’s identity portfolio.
NHIs ensure seamless operations within modern organizations, and their significance has only been magnified with each technological leap—cloud computing, DevOps, robotic process automation (RPA), Internet of Things (IoT), and next-gen AI advancements. But when compromised they can silently springboard an adversary into the heart of a company's most sensitive operations. For example, Cloudflare’s security incident last fall was a result of attackers using the access afforded by access tokens and service account credentials to infiltrate its systems.
Complicating matters is that companies often lack a comprehensive inventory of NHIs, and don’t have a map of all the resources they can access and the actions (permissions, entitlements, etc.) they’re authorized to perform. As a result, organizations must treat NHIs as first-class citizens to preserve their security, operational integrity, compliance, and efficiency in digital endeavors.
About Rezonate
Rezonate is a leader in identity-first security, committed to helping organizations defend against attackers while making it easier to proactively protect identities. The platform provides a full set of modern solutions including identity security posture management (ISPM), identity threat detection and response (ITDR), and compliance. Learn more at www.rezonate.io.
View source version on businesswire.com: https://www.businesswire.com/news/home/20240716267123/en/
Contacts
Treble
Jim Cameron
rezonate@treblepr.com